“Identity is the new perimeter, like network used to be. Hybrid or remote work has been a catalyst to pushing that, so that’s where the bad actors are going.”
Recent industry analysis shows credential theft and identity abuse now power the majority of major breaches, a trend backed by multiple 2025 identity reports. Attackers increasingly skip noisy exploit chains and simply log in using stolen credentials, abused integrations, or forged tokens. Once inside, they move laterally, elevate privileges and exfiltrate data.
A vivid example landed recently with the Salesloft/Drift incident: attackers stole OAuth tokens from a third-party integration and used those tokens to query and export sensitive Salesforce data across hundreds of organisations.
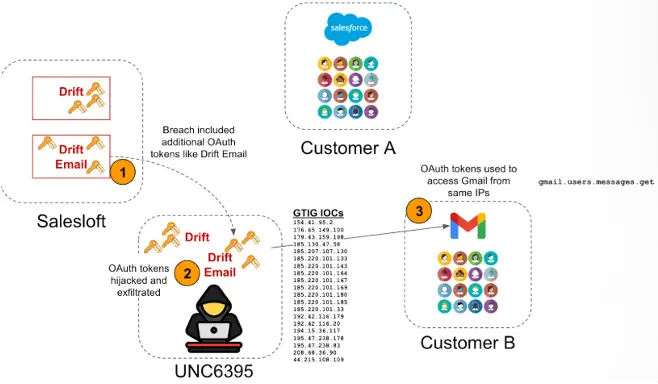
The breach underscores two painful truths for MSPs and their customers:
1. Trusted integrations can become attack conduits, and
2. Conventional defences (firewalls, email gateways, EDR) often miss token abuse that looks like legitimate activity.
That’s why ITDR — Identity Threat Detection and Response — matters.
ITDR is a class of detection, investigation, and response focused on identity systems: accounts, credentials, tokens, privileged access, and the abnormal behaviours that reveal compromise. Unlike standalone IAM or MFA controls, ITDR continuously monitors behaviour, connects events across identity sources, and enables rapid automated or human-led containment before attackers escalate.
“In 2024 Microsoft saw an average of more than 7,000 password attacks happen per second.”
Why are Identity attacks so challenging?
Here are the practical reasons ITDR matters — and the ways Manage Protect protects MSP clients with Guardz:
- Identity attacks are noisy and subtle
Simple alerts (a suspicious login, an “impossible travel” flag) produce massive false positives if treated in isolation. By connecting multiple signals – device telemetry, user agents, IP history, mailbox behaviour and EDR data – the Guardz algorithm decides whether activity represents risk. The platform turns dozens of raw events into one user-centric incident so MSPs know who to act on and why. - OAuth/token theft is a growing attack vector
OAuth token theft (including device code flow abuse) can grant attacker access in seconds. Because these flows are legitimately used for integrations, token abuse can look like normal activity… unless you have detection tailored to token lifecycle, anomalous token usage, and correlated downstream actions (e.g., mass exports, mailbox rule changes). - The landscape keeps changing
Guardz’s research and threat-hunting team uses agentic AI to surface new attack tradecraft across the customer base, then converts those discoveries into ITDR rules. AI also triages and enriches millions of events per second so humans only see prioritised, contextual incidents. That combination shrinks time-to-detect and time-to-remediate. - Response needs to be surgical and reversible
For MSPs, effective containment must avoid breaking customer productivity. Guardz supports reversible, high-impact actions (suspend user, isolate device) that stop lateral movement immediately and are easy to roll back. MSPs can pre-authorise actions for the MDR team or require approval — giving flexibility for different SLAs and client comfort levels. - Make incidents explainable and operationally useful
Guardz presents incidents in timelines and graph views, bundles playbooks and PDF incident reports, and provides analyst guidance so MSP teams can complete remediation and, if needed, re-escalate to the SOC. The user-centric view (everything wrapped around a named employee) makes customer communications and post-incident reporting far simpler.
What this means for MSPs
For MSPs protecting small and mid-market customers, these capabilities are more than feature-creep – they’re essential. The modern attack surface includes SaaS integrations, API tokens, and federated auth flows; when teams rely on manual playbooks or siloed logs, attackers win time and access. ITDR makes identity the priority lens for detection and response, stopping intruders who “log in” rather than “break in.”
WEBINAR ON DEMAND
Guardz presents... ITDR in Action
Learn how Guardz leverages AI to connect the dots, turning multiple isolated alerts into one clear, actionable narrative. Doni Brass at Guardz presents this session and demos their ITDR capabilities.







